Ransomware has been a fast growing threat to both businesses and individuals with billions in global projected losses in 2017 alone. Unlike ransomware of the past that would simply attempt to scare users into paying with fake FBI or Virus warnings, modern ransomware locks the user's files preventing access unless the ransom is paid. The methods used to lock the files are impossible to break and even the FBI has suggested to “Just pay.”
Q: What is Ransomware?
A: Ransomware is a type malware that locks a user's files unless a ransom is paid.
Instances of ransomware infections have been rising and have made national news last year after an entire hospital's digital records became infected forcing them to pay $17,000 to regain access to the files. The effects of this type of attack are devastating for both business and personal users, imagine the cost of losing all of the files on your computer or business server.

The Hollywood Presbyterian Medical Center paid $17,000 to attackers to regain access to patient and hospital data.
We see the ransom being paid very often because the cost of lost files and time is worth more than the cost of the ransom paid. This is why the threat continues to grow and evolve, there is simply too much money to be made. According to the FBI, ransomware victim payouts totaled $209MM in the first quarter of 2016 alone, while Datto a backup solution provider estimated the total impact to be in the billions once factoring in time and productivity loss to the infected businesses.
Paying a $17,000 ransom such as the targeted case against the hospital is rare. Most ransoms paid are between $1,000 to $5,000 as reported by a Datto survey of IT professionals. This is a deliberate strategy by the attackers. By pricing the ransom lower they have a greater chance at receiving payment, to most business owners their data is worth much more than $5,000.
Q: What can I do if I am infected?
A: Restore from backups or pay.
If you have proper backups you can usually restore from those and your only loss is the time. However, if you do not have uninfected backups you are forced to pay or start over. This is the only answer once infected and why maintaining proper backups and having a solid disaster recovery plan is more important than ever. One common question we receive from victims is “Why can’t you just crack it?” and the answer is that due to how these programs encrypt data even a supercomputer would take years to decrypt it.
As previously reported by CCN, special agent at FBI’s Cyber and counterintelligence program, Joseph Bonavolonta, said:
"The ransomware is that good. To be honest, we often advise people just to pay the ransom."
If paying is your only option the ransom may be justifiable but even after deciding to pay there is no guarantee that the attacker will follow through with unlocking the files. There is also the lengthy process of buying bitcoins, the digital currency that is usually demanded, and waiting for the attacker to send the unlock password that can take days.
Q: How would I become infected?
A: Below are some of the common ransomware attack vectors.
- Web or Email Phishing
- Infected Email Attachment
- Malicious Websites
- Infected Downloads
- Weak network security
- Disgruntled Employee
- Outdated/unpatched or otherwise vulnerable software
The most common way we’ve seen ransomware spread is through infected emails. The attacker will send out mass emails containing infected attachments or links to malicious websites containing infected downloads. These emails work because they are disguised as legitimate mail usually containing a subject to entice unsuspecting employees to open including invoices, HR/Payroll, vendor payments, contracts, etc.
While email is common due to its heavy use and reliance in business, ransomware
is still spread widely through other means. Weak network security such as open or unmonitored ports on servers, misconfigured wifi, or unpatched software and operating systems can also lead to infection. Although less common ransomware can be spread willingly by a disgruntled employee or 3rd party with access to the network or company email. Some enterprising criminals have started “Ransomware as a Service” type businesses on the dark web. These services provide the actual ransomware virus and payment backend to the customer in exchange for a share of the ransom, while it is up to the customer to distribute as they see fit. This system allows even non-tech-savvy users the ability to anonymously sabotage a business and potentially profit while doing so.
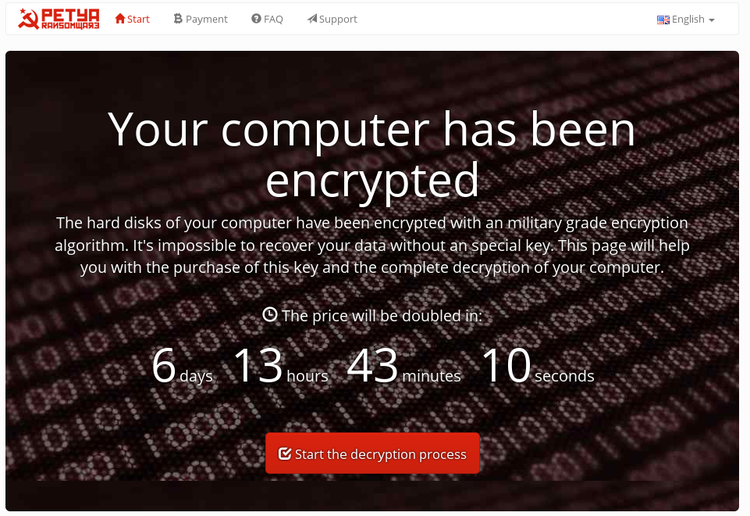
An example of the payment screen presented after a computer has been locked with Petya Ransomware.
Q: How do I protect myself against ransomware?
A: While there are a few specific security measures that are directed toward ransomware, prevention is the same as protecting against any other security threat.
- Email, Web & Network Protection
- Spam Filter
- Firewall
- Internet Filter such as Cisco Umbrella
- Endpoint & Server Protection
- Anti-Virus Program
- Block Browser Ads and Popups
- Low privilege user rights
- File change monitor
- Regular patching and updates
- User Education & Training
- Robust Backup and DR Plan
While it's important to do everything possible to reduce the chance of infection two of the best defenses against ransomware are user education and robust backups and disaster recovery. As you have already read the most common attacks rely on unsuspecting users visiting a malicious site or opening an infected email. Users should be taught how to spot the red flags of infected emails and links and what to do if they think they receive one.
What you can do.
The most effective prevention that every user can do is to educate themselves on the red flags and telltale signs of infected sites, emails, and attachments. Take time to read the full URL of links and to never open or run any unknown or unexpected attachment. One easy method of determining if a link or file is infected is to use the website VirusTotal. The website will scan the file using many different AV databases. Just remember to proceed with caution and the best course of action is to contact your I.T. department immediately. We also recommend ditching Internet Explorer and using a modern internet browser such as Google Chrome as it is more secure and supports the use of security plugins such as FlashControl and Ad Blockers.

What your I.T. Team can do
From a technical standpoint we’ve seen that the implementation of an email spam filter and network filter such as Cisco Umbrella is the best way to mitigate ransomware infections. We also suggest strong network security policies on desktops and servers as well as firewalls and network appliances, including securing any wifi networks. All users should also use low privilege non-admin accounts on their workstations. Restricted accounts can prevent the infection from spreading and contain the damage to one workstation. Although more advanced, monitoring servers for suspicious file changes and implementing automated procedures if detected can prevent the spread of an infection. Not to be forgotten, regular updates and patching can prevent outdated software from being exploited. Lastly while not as effective as the other methods workstations should be monitored with an anti-virus program. Your I.T. team should also lead user education training sessions to raise awareness of the threats and outline the proper procedure if a user suspects an infection.
We have to remember that no method is perfect and there is the risk of infection on even the most secure networks. This is why above all it is important to have and maintain a proper backup and recovery plan. Backups should follow the 3-2-1 rule, 3 total copies, 2 different media, and 1 backup in a different location. Backups are worthless however if they cannot be restored fully or in a timely manner. Backups should be tested regularly and be able to be restored quickly. Although convenient and cheap, cloud only backups can take days to restore dependant on your internet connection. Because of this, we suggest an on-site backup as well as off-site.
Stay safe!
Considering Managed IT Services For Your Business?
Take advantage of our free offer valued at $599.95. No cost, no risk, and no obligation to you.



